| Getting your Trinity Audio player ready... |
Imagine having a fortress for your digital assets, a place where your data is untouchable and your applications run smoothly without fear of cyber threats. This is the promise of a Virtual Private Server (VPS), but the reality is that many businesses are still navigating the complex landscape of VPS security. With cyberattacks becoming increasingly sophisticated, securing your VPS is no longer a luxury—it’s a necessity.
In this article, we’ll unveil ten crucial tips to fortify your VPS against unauthorized access and cyber threats. Additionally, we’ll expose the eight most common vulnerabilities lurking within virtual servers.
By understanding these risks and implementing our expert advice, you’ll transform your VPS into an impenetrable fortress. Read on to discover how to safeguard your digital kingdom.
Top Strategies to Secure a VPS Server
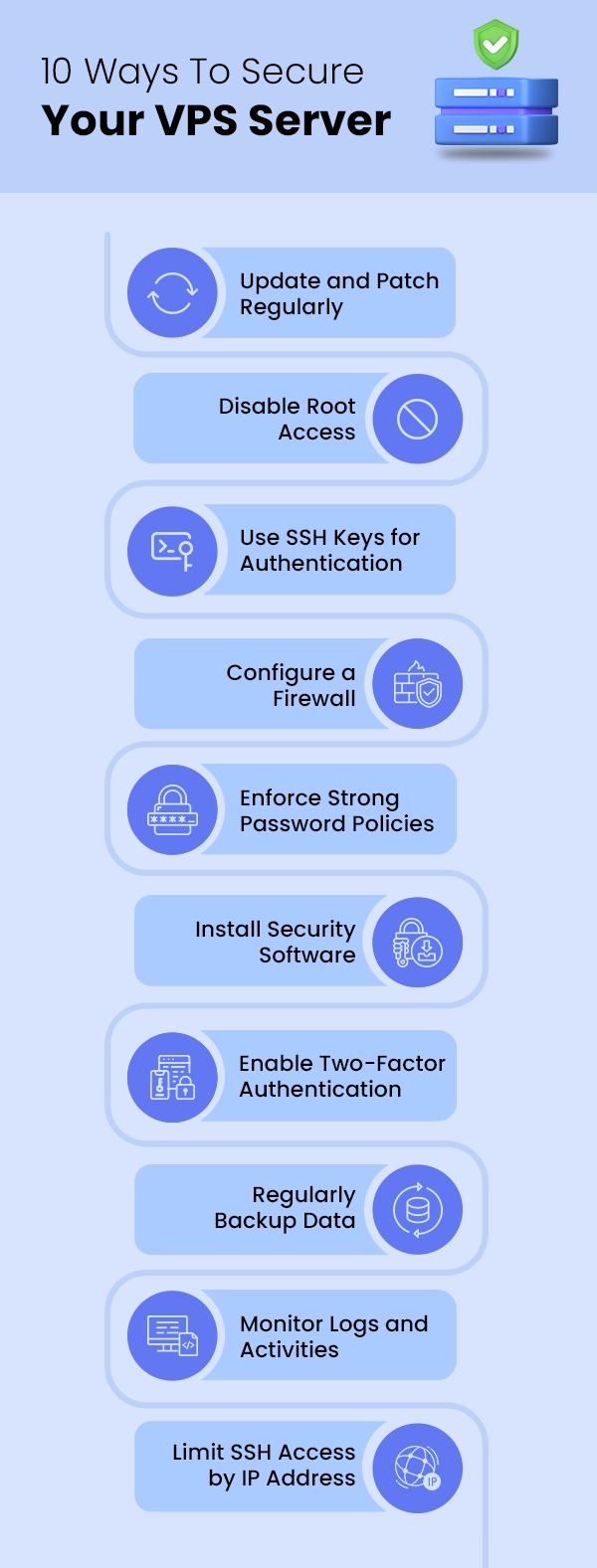
1. Update and Patch Regularly
Outdated software might carry multiple vulnerabilities that can lead to cyber-attacks. Update and perform regular security patches on your software, applications, and operating systems. It will help improve your VPS security, stability, and performance.
Developers keep on releasing updates from time to time. Check for the availability of any latest versions available and install them to tighten your server security.
Consider automating the update process when using a Content Management System (CMS). It will relieve you from the regular burden of performing updates while keeping your data secure at all times.
Also Read: How To Choose VPS Hosting? – A Complete Guide
2. Disable Root Access
A root user has the ultimate power to make any changes to the VPS. That is why cybercriminals try to get access to a server as root user. If they crack the root password, they will gain access to the whole of your server.
It is, therefore, necessary to eliminate the most common target of VPS hackers by disabling root access. Consider using a non-root user account carrying all the necessary permissions.
Carry out server configuration tasks by granting this new user the privilege to execute root-level commands. Don’t forget to give this user a random username to keep everything secret.
Also Read: What Is A VPS Server Used For? Everything You Need To Know
3. Use SSH Keys for Authentication
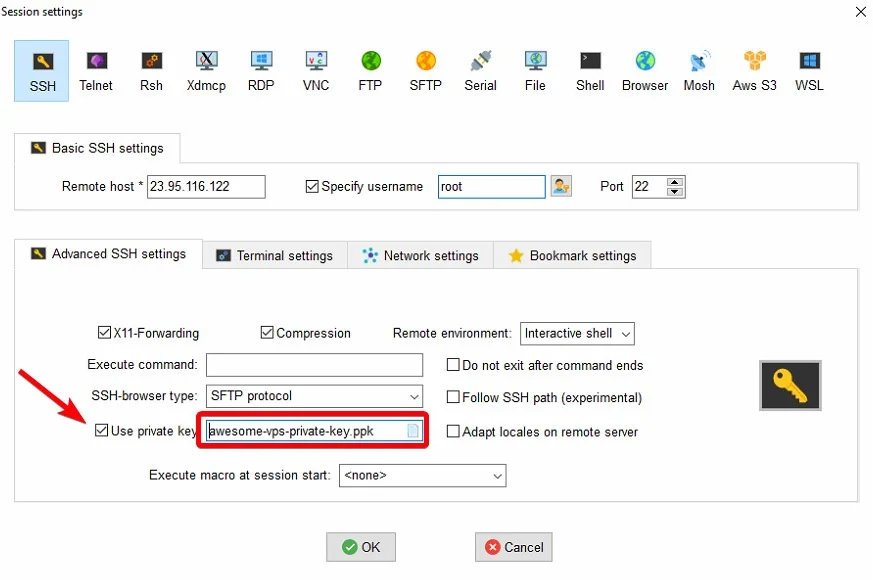
Using a password to log in to your SSH account exposes your VPS to sniffing attacks. Therefore, it is advised to use SSH keys for VPS authentication to prevent this issue.
SSH keys are computer-generated encrypted keys that are very complex and hard to crack compared to a root password. They come in pairs of two with one being a public key and the other a private one. The public key is stored on the VPS and the private is saved on your computer.
The server generates a random string on detecting a login attempt and encrypts it with a public key. This encryption can only be decrypted with the related private key. Such complex encryption of SSH keys helps in protecting phishing and brute-force attacks.
Also Read: VDS Vs VPS: Choosing The Right Virtual Server
4. Configure a Firewall
A firewall acts as a barrier between your VPS and traffic. It checks all inbound and outbound traffic and filters it to protect your server. Configuring a firewall involves setting up security rules to prevent your VPS from potential DDoS attacks and malicious traffic.
A well-configured firewall ensures passing only secure and legitimate server requests, blocking all suspicious connections. It is also necessary to regularly monitor and update your firewall settings to ensure continued protection against evolving cyber threats.
You can significantly enhance your server security by using private web hosting that will keep your personal data safe, on top of that, you can configure your VPS firewall to prevent any potential breaches.
Also Read: How Does A VPS Work? A Complete Guide For Beginners
5. Enforce Strong Password Policies
Enforcing strong password policies is essential in securing your VPS from potential cyber threats. Set up certain requirements such as minimum character length and use of letters, numbers, and special characters.
Also, prohibit the use of common or easily guessable passwords. Consider creating long passwords and avoid using the same password for different accounts. It is also important to implement password expiration policies.
The National Institute of Standards and Technology (NIST) recommends creating long passwords in the form of easy-to-remember phrases. Use a four-to-five-word long phrase for accounts with root privileges to make it difficult to crack.
Also Read: Best Practices To Secure Your Website
6. Install Security Software
Installing security software like Fail2Ban helps protect your VPS from brute force, dictionary, and DDoS attacks. Fail2Ban is a powerful intrusion prevention tool that secures a server by monitoring server logs for suspicious activity. It effectively blocks IP addresses that exhibit malicious behavior like multiple failed login attempts or brute force attacks.
Additionally, deploying antivirus software on your VPS can further bolster its defenses against malware, viruses, and other malicious entities. A reliable, open-source solution like ClamAV can help strengthen VPS security while saving costs. It will monitor all files on your server and quarantine the unwanted ones while also detecting suspicious activity otherwise.
Also Read: 10 Ways To Secure Your E-Commerce Website
7. Enable Two-Factor Authentication (2FA)
Enabling two-factor authentication to log in to your VPS will significantly enhance its security. Under this method, you need to verify your login attempt with a unique code in addition to a password. Such a code is typically sent to your registered email or device.
Using 2FA adds an extra layer of protection to your VPS and reduces the risk of unauthorized access. Even if an attacker manages to acquire your login credentials, he won’t be able to get the unique code.
Also Read: 9 Types Of SSL Certificates – Make The Right Choice
8. Regularly Backup Data
Regularly backing up data is a crucial practice for securing your VPS and safeguarding against potential data loss. By creating frequent backups, you can protect important files, applications, and configurations from unexpected system failures or cyber-attacks.
Implementing a consistent backup routine enables you to quickly restore your VPS to its previous state without losing valuable information. Consider automating the backup process and storing copies of data in secure storage locations like external drives or the cloud.
Additionally, regularly testing the restoration process of your backups ensures their integrity and effectiveness. Consider maintaining copies of only the recent server data to keep your backup maintenance costs minimal. Also, the restoration process must be quick and easy for faster data retrieval.
Also Read: Top 5 Reasons Business Owners Need Website Backup
9. Monitor Logs and Activities
Regular monitoring of server logs and activities helps to secure your VPS. Logs are the activity records of your server. It is possible to detect and respond to potential security threats instantly with efficient log auditing.
Monitoring also allows you to locate unusual patterns for early detection of potential security breaches. Consider keeping an eye on login attempts, file modifications, resource usage, and network traffic. Identifying and fixing VPS vulnerabilities sooner will minimize the chances of server attacks.
Organizations can proactively protect their data and infrastructure from cyber threats by actively monitoring logs and activities on a VPS. Consider utilizing advanced tools like Intrusion Detection Systems (IDS) and log analysis tools for comprehensive VPS security management.
Also Read: VPS Hosting VS. Dedicated Hosting – 6 Key Factors To Consider
10. Limit SSH Access by IP Address
Limiting SSH access by IP address is a crucial step in enhancing the security of your VPS. You can significantly reduce the risk of unauthorized access by restricting SSH connections to only trusted IPs.
This measure provides better control over who can log into the server and helps prevent malicious actors from gaining entry. You need to set up firewall rules or utilize tools like TCP wrappers to implement this security measure.
Regularly reviewing and updating the list of allowed IP addresses is also essential. It will ensure that only authorized users have access to the server.
Also Read: Difference Between VPS And WordPress Hosting
Common VPS Vulnerabilities You Should Know
Attackers are always looking to exploit server weaknesses to gain unauthorized access to a VPS. Therefore, it is important to be aware of common VPS vulnerabilities to fully protect it:
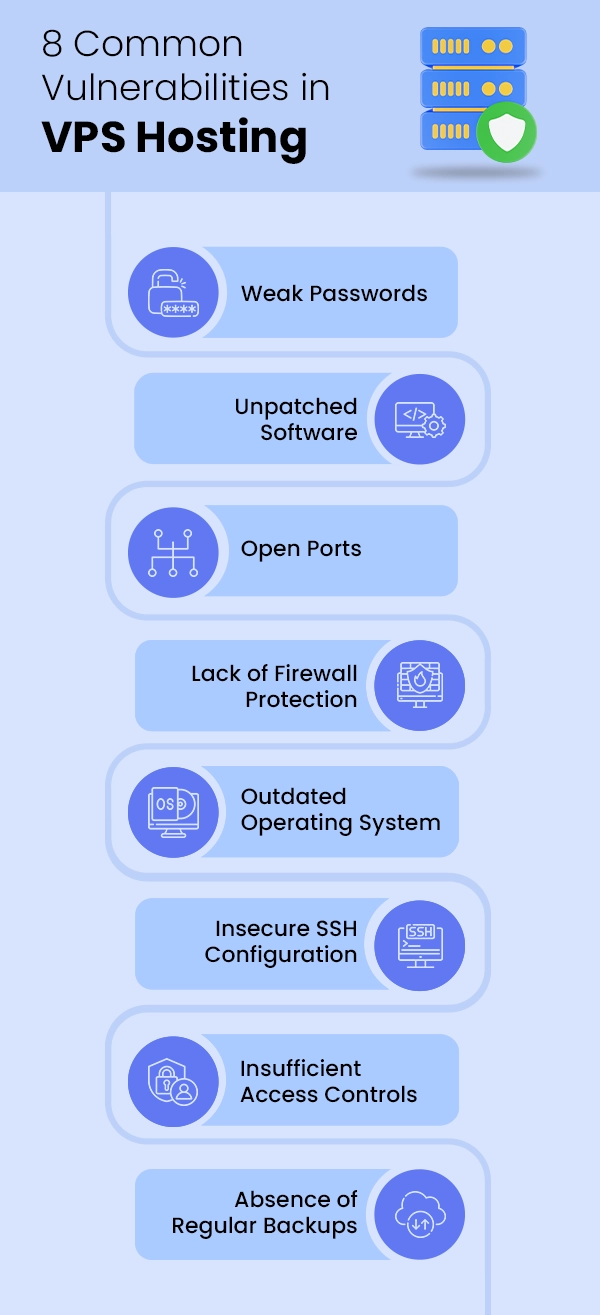
1. Weak Passwords
Using weak passwords is among the most common VPS vulnerabilities since hackers will crack them easily. A survey conducted by the UK’s National Cyber Security Centre (NCSC) revealed that 123456 is the most commonly used password. Of all survey participants, a whopping 23.2 million accounts used it.
So if you are serious about protecting your VPS data, never use such common passwords. Avoid using your name, birth date, or other easy-to-guess information as your login details.
2. Unpatched Software
Using unpatched software poses a significant security risk for your virtual server. Developers regularly release updated software versions with security patches to help prevent data breaches. This vulnerability occurs when you do not update an operating system, plugin, or application to its latest version.
Hackers can easily exploit these unpatched vulnerabilities to enter your server and execute malicious code or steal sensitive data. The consequences of such breaches can be severe, including loss of reputation, financial damage, and legal cases against your company.
Therefore, it is important to regularly update your VPS software and conduct routine security audits to identify any weaknesses. It will help you mitigate the risks associated with unpatched software and secure your VPS effectively.
Also Read: What Is Bandwidth In Web Hosting? Things You Must Know
3. Open Ports
Open ports are among the most common vulnerabilities found in a VPS. An open port is a communication endpoint that allows data to flow in and out of a server.
When these ports are left unprotected, hackers can easily gain unauthorized access to the server and exploit its resources. This type of vulnerability can lead to numerous cyber attacks like malware injections, DDoS attacks, and unauthorized data exfiltration.
Therefore, it is crucial to regularly scan your VPS for exposed ports. Consider securing them with firewalls, intrusion detection systems, and access control lists.
4. Lack of Firewall Protection
Firewall protection is an essential component of any VPS security framework. Lack of firewall protection makes your server vulnerable to multiple cyber threats, including malware injections and data breaches. It can expose sensitive information and compromise the integrity of the entire server.
Hackers often exploit this vulnerability and enter your VPS via backdoors. Thus, it is essential to implement robust firewall protection mechanisms that can effectively monitor incoming and outgoing traffic.
A firewall must also be capable of blocking malicious IP addresses to prevent unauthorized access to the server. By prioritizing firewall security, you can significantly reduce the risk of cyber-attacks and safeguard your data from potential threats.
Also Read: How Much Storage Do I Need For My Website? Must-Know Factors
5. Outdated Operating System
An outdated operating system is another common VPS vulnerability. Such systems are susceptible to security breaches due to unpatched vulnerabilities that have been fixed in newer versions.
Hackers often target servers running outdated operating systems as they know these systems may lack necessary security updates and patches. To prevent this, consider updating your operating system regularly and minimize the security risks involved.
6. Insecure SSH Configuration
Insecure SSH configuration is a common vulnerability frequently encountered in a VPS. SSH, or Secure Shell, is the primary method for remote access to virtual servers. When configured improperly, it can lead to unauthorized access by malicious actors.
This vulnerability can result from weak passwords, outdated encryption algorithms, or using default settings that are easily exploitable. Therefore, you must adhere to best security practices like enforcing strong password policies and enabling two-factor authentication. Also. Disable root login and regularly update SSH configurations and software.
Also Read: 10 Best Web Hosting Control Panels (Paid+Free)
7. Insufficient Access Controls
Inadequate access controls mean a lack of proper restrictions placed on user permissions. It is a common VPS vulnerability that can lead to manipulation of system settings by hackers. It can occur due to misconfigurations, weak password policies, or outdated software on a server.
Insufficient access controls can result in unauthorized data exfiltration, system downtime, or even complete loss of valuable information. Eliminate this vulnerability by regularly reviewing and updating access control policies. Additionally, strong authentication measures should be enforced, and user activities should be monitored for any suspicious behavior.
8. Absence of Regular Backups
The absence of regular backups poses a significant vulnerability for virtual servers. Without regular backups, a VPS is at risk of losing important files, databases, and configurations in the event of cyberattacks.
This vulnerability can disrupt business operations, compromise sensitive information, and result in costly downtime. Thus, ensure to establish a comprehensive backup strategy that includes frequent automatic backups stored in secure offsite locations. It will help you recover your data even after a cyber attack.

Conclusion
Securing your VPS involves implementing best practices like using strong passwords, regularly updating software, enabling firewalls, and encrypting data. Additionally, monitoring for suspicious activities and conducting routine security audits are essential to proactively identify vulnerabilities before they are exploited.
Finally, remember that securing a VPS is not only a good practice. Rather, it is a critical component of an organization’s comprehensive cybersecurity strategy. So consider focusing on it on an ongoing basis.