Highlights
- Website breaches can cause massive financial loss, legal trouble, and long-term damage to your brand reputation.
- Weak logins, poor password practices, and a lack of authentication are the biggest reasons websites get hacked.
- Strong authentication (HTTPS, MFA, secure passwords, and rate limiting) protects user data, builds trust, and helps businesses avoid costly breaches.
- In short, building a secure login system is essential & not optional. So, to keep your website, users, and brand safe.
Introduction
How bad can a website breach possibly be?
Well, really bad!
In 2014, Home Depot, a multinational home improvement retail corporation, suffered a breach that resulted in the theft of over 56 million payment card records from its database by cybercriminals. The retail brand spent about $180 million settling damages.
MySpace, initially a social media platform, lost nearly 360 million user logins, names, and dates of birth (DOB) to attackers. This happened because the platform used older unsalted algorithms like SHA-1 to encrypt its users’ login details, and the impact negatively smeared MySpace’s reputation.
A similar incident affected First American Financial Corp. in 2019, when 885 million files, ranging from bank account numbers to licenses and wire transfer receipts, were exposed due to a website design error called IDOR (Insecure Direct Object Reference). IDOR allowed direct access to private information without requiring authentication. The company was fined $500,000 by the SEC.
Each breach costs you financially, puts you at risk of lawsuits, and damages your existing brand image. Even worse, it can herald a business shutdown. And that’s why you need to create a secure login for your website proactively.
In this article, we’ll share practical steps to do that and highlight the best security practices to implement.
What is a Login System?
A login system is a security guardrail used to protect your website by identifying and verifying users’ identities before granting them access. This includes frontend data collection boxes where users input their usernames and password to access your website.
On the backend, your system validates these credentials against stored, encrypted data, manages session tokens, and applies additional safeguards such as rate limiting, multi-factor authentication, and secure password hashing.
Also Read: How You Can Find Bugs in Websites Manually?
Why Strong Authentication Matters?
In May 2024, the threat group UNC5537 breached Snowflake by exploiting customers who lacked strong credential management and multi-factor authentication. This allowed the hack group to steal sensitive data and extort over $2.7 million from the victims. Snowflake also became a target for legal implications.
So, poor authentication results in:
- Financial expenses on your users’ ends due to extortion.
- Financial expenses on your end for breach settlements, placations, and hackers’ demands.
- Legal implications, including lawsuits.
Anna Zhang, Head of Marketing at U7BUY, says, “The cost of poor authentication far outstrips monetary expenses and lawsuits. Every breach scars your reputation and makes your website less trustworthy.
Trust is critical to the survival of your business, especially if you offer services in the e-commerce niche and other industries where customers rely on secure interactions.
Flip the switch to strong authentication, and you gain:
- A more secure website with protected user data.
- Greater trust in your services and how you handle sensitive information.
- Reduced risk of breaches, fraud, and account takeovers.
- Compliance with data protection and industry regulations.
- A stronger brand reputation that attracts and retains customers.
- Long-term cost savings by avoiding legal, technical, and recovery expenses.
Besides, you’ll be able to redirect your resources and focus on what matters most.
Also Read: Which Functions are the Important on a Website?
Difference Between Authentication and Authorization
Authentication is the process of identifying and verifying a user’s identity through the data they input.
➔ The data can be anything from usernames and passwords to simpler biometric details like eye scans and fingerprints
➔ Once your system matches their data against the one in your database, access is provided
On the other hand, authorization determines the kind of access your users have after authentication.
➔ It specifies what users can do or not do, which pages of the website they can access, resources they can use, and any other data
➔ Their level of access is controlled by roles, permissions, and policies set within the system
To make things easier, authorization is like an inner gate that protects core details even after a user has gained access to the general dashboard. Or you can say it acts as a second protective layer, ensuring hackers or unauthorized users can’t move freely or reach sensitive areas beyond their permitted access, thus mitigating loss in the event of a breach.
Every difference in a nutshell:
| Feature | Authentication | Authorization |
|---|---|---|
| Definition | Process of verifying a user’s identity | Process of determining a user’s access rights |
| Purpose | Confirms who the user is | Controls what the user can do |
| Process | Done through credentials like passwords, biometrics, or tokens | Done through roles, permissions, and policies |
| When it occurs | First step before granting access | Follows authentication |
| Result | Grants or denies login | Grants or restricts actions and resource access |
| Visibility to the user | Visible (user enters credentials) | Often invisible (system applies permissions) |
| Protective role | Acts as the first security layer | Acts as the second security layer |
Also Read: Important Things Business Websites Should Have
10 Essential Steps to Create a Secure Login
Creating a secure login system is non-negotiable if you want to provide a safe website for your users and protect yourself.
Here are some steps to do that:
1. Use HTTPS (SSL Certificate)
HTTPS stands for Hypertext Transfer Protocol Secure, a more secure version of HTTP. The protocol utilizes encryption services such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS) to secure data transmission between your website’s server and a web browser. This prevents hackers and threat actors from eavesdropping on your login credentials.
To implement HTTPS, you need to buy an SSL certificate from a trusted Certificate Authority, install it on your server, and configure your website to automatically redirect all traffic from HTTP to HTTPS.
However, that’s a lot of work, and it might also cost some money. Instead, consider subscribing to hosting service providers like Host IT Smart, which offers a free SSL certificate with your preferred hosting plan or can be purchased separately.
Also Read: Which SSL Certificate Is Best For An eCommerce Website?
2. Secure Password Storage
When a user creates a login credential on your website, their username and password are automatically saved by default in plain text on your database. In the event of a system hack where attackers gain access to your database, they can easily extract these credentials and use them for any purpose.
To prevent that, you can implement:
➔ Hashing: Convert passwords into fixed-length, unreadable strings using strong hashing algorithms such as bcrypt, scrypt, or Argon2.
➔ Salting: Add a unique random value (salt) to each password before hashing to prevent attackers from using precomputed tables (rainbow tables).
Suppose you use hashing; a regular password like ‘mypassword’ becomes something like ‘a2cde6fykj6j%jsyik’. If a user logs in again, their password is hashed the same way, and the system just compares the two hashed results.
You can also engage in iteration by hashing multiple times to slow down brute attacks.
3. Enforce Strong Password Policies
Think of passwords as keywords. Hackers now use automated tools to search for common, predictable weaknesses, like default usernames or simple passwords they can exploit, similar to how marketers use a keyword research tool to find keywords.
So, if your users utilize passwords like admin.ph, 1234, or their surnames, they are literally handing hackers their key. Avoid that by implementing these policies:
- Minimum length: Require at least 8–12 characters. Longer is stronger
- Complexity: Encourage a mix of uppercase, lowercase, numbers, and symbols
- Avoid common passwords: Block simple or widely used passwords like “123456” or “password”
- No reuse: Prevent users from recycling old passwords or using passwords across platforms
- Regular updates: For sensitive accounts, prompt users to refresh passwords after a specific period
Cybercriminals will find it harder to randomize “Icedcoffee#92@@” compared to “Icedcoffee1234”.
Also Read: Ways to Prevent Website Crash From Traffic?
4. Implement Multi-Factor Authentication (MFA/2FA)
If you run a business with a warehouse full of valuable inventory, such as your line of branded merchandise, for example, you would never secure that physical warehouse with a single, inexpensive padlock. Why? Because a single layer of protection is never enough.
Likewise, with website security, a single security policy is weak, and hackers can bypass it in multiple ways that you may not be prepared for.
That’s why you need to implement a double-layered security system—the credential login and a second authentication to reconfirm users’ identities. This is called multi-factor authentication and has three components:
- Something they know: Username and password or PIN
- Something they have: Hardware token, their phone, or an authentication app like Google’s authentication app
- Something they are: Biometrics like face or fingerprint
You only need any two of the three components to make 2FA work. For instance, you can request users to log in with their credentials and then use Google’s authenticator app to complete their login. Or request credentials and biometrics.
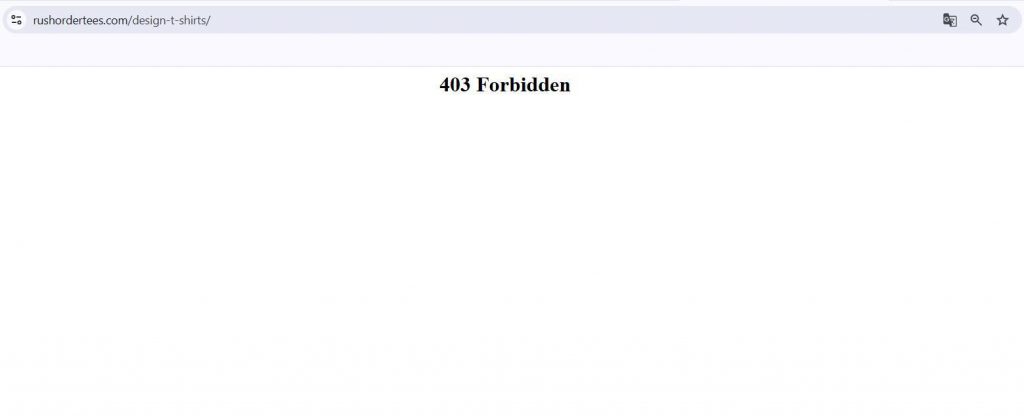
If your website serves customers only from specific regions, you can limit access for users from other countries. For example, if you sell custom printed apparel only in the U.S. and Canada, you can block visitors from outside these areas. This helps protect your business from unwanted traffic. It also improves website performance and security.
As shown in the screenshot of the RushOrderTees T-shirt page, visitors from outside the U.S. or Canada see a “403 Forbidden” error message.
At the same time, American and Canadian users have unrestricted access to the website.
Also Read: What Makes a Good Website Checklist?
5. Limit Login Attempts & Brute Force Protection
For a brute force attack, cybercriminals attempt different variations of likely login credentials, one by one, until they find one that works and grants them the necessary access. Sometimes, brute force attacks can be much complex and be in the form of:
- Dictionary attack: tools test common passwords and phrases from curated lists rather than every possible string
- Credential stuffing: attackers try to use leaked username and password pairs from other breaches against your site
- Hybrid attacks: combine dictionary words with common tweaks, such as appending numbers or characters
- Distributed attacks: attempts originate from multiple IP addresses to circumvent per-IP rate limits
You need to modify your login system to limit the number of login attempts. Once exceeded, a cooldown period should be triggered, which can last from several minutes to a full day. During the cooldown period, the attacker is unable to continue punching in their list.
If there’s a recurrence, lock the account and contact the user for further details. To make this easy, employ brute force protection services like Cloudflare, a web application firewall, or Auth0, an identity and authentication service provider.
Also Read: Top Technical Requirements For eCommerce Websites
6. Secure Login Forms
Login forms are the front door to your whole security system. Once you leave it poorly designed, the risk of a breach also significantly increases. So, beyond the CSS and HTML, employ secure methods like:
- Enable input validation and sanitation. This prevents SQL injection and cross-site scripting attacks
- Lockouts and CAPTCHA to eliminate automated brute force attacks and bots
- Notify users to cross-check the website URL before inputting their credentials. It should be the correct URL and delivered over HTTPS
- Hash login credentials as users type them
Additionally, limit the number of add-ons, plugins, and elements on your login page, as they can make the page more vulnerable to attacks. For instance, WooCommerce plugin bug issues led to data from over 5 million websites being exposed to theft in 2021.
Also Read: Ways to Secure an eCommerce Website
7. Follow Session Management Best Practices
Grant Aldrich, Founder of Preppy, says, “When a user logs in, your system automatically creates a session for them. However, many things can happen during a session. Your users might switch tabs to other websites or applications, go passive for some time, and leave the session open without proper oversight, or even forget to close the session when they are done.”
“These errors present hackers with a perfect opportunity to hijack already created sessions and access your database”, Grant continues.
And that’s why you need to implement session management practices such as:
- Setting HttpOnly and Securing flags on cookies to prevent JavaScript access and block transmission over unsecured connections
- Setting the SameSite attribute to reduce the risk of cross-site request forgery (CSRF)
- Implementing session timeouts, which automatically expire sessions after a period of inactivity
- Re-authentication for sensitive actions by prompting users to re-enter credentials for high-risk actions, like password changes or transactions
- Invalidating sessions on logout by ensuring tokens are destroyed server-side once users log out
You should also monitor for suspicious activities, such as the same account being active in multiple countries simultaneously.
Also Read: Common Reasons for a Website Crash
8. Monitor & Log Login Activity
Login activity can help you dig out suspicious login attempts. For instance, a sudden spike in login attempts on an account signifies a possible brute force attack. Looking into it can help you prevent unauthorized access.
For optimal results, track all login and logout attempts and securely log them. Study patterns, especially those that look suspicious or unexpected. You can forward the logged data to security monitoring systems, such as Azure or Splunk, for analysis.
Also Read: Website vs Web Application
9. Enable Single Sign-On (SSO) Options
Single Sign-On options enable users to access your website with login details provided by secure services like Google or Microsoft. This eliminates the need to create separate passwords for services and streamlines the login process, as users can use the same credentials for multiple services.
Additionally, centralized login reduces password creation fatigue and facilitates the enforcement of stronger security policies.
To implement this, you can utilize OAuth 2.0, which enables secure delegated access on your login page. Other methods include OpenID Connect, a simpler identity layer built on OAuth 2.0, and SAML, also known as Security Assertion Markup Language, which is widely used by large enterprises.
Also Read: Difference Between Web Application and Desktop Application
10. Regular Security Audits & Updates
Every day, hackers devise new methods to circumvent your current security measures. Once your system is unable to keep up, you risk having a breach. So, your website is only as secure as how often you audit it.
Take monthly or quarterly turns auditing every security policy you’ve implemented and ensure they’re in place. Look out for new ways hackers are exploiting security weaknesses and fix them on your page before you take a hit.
You can create an internal testing space where you brute force your website, throw all sorts of attacks at it, and measure its endurance ahead of any unwanted but possible D-Day.
Also Read: Types of Information eCommerce Sites Need to Protect
Best Practices for User-Friendly Secure Logins
Security is a two-way effort—you and your website users. To help them comply with the policies you’ve created, consider the following:
➢ Keep the Login Process Simple
Don’t overcomplicate the login process just because you want to make it secure. If the process of MFA or 2FA seems too complex, consider introducing options like SSO to keep things concise and straightforward. Your CAPTCHA should not be too easy for bots to read, but also not too complex for users to understand.
➢ Allow Password Managers
Every time a user creates a new set of login credentials on your website, allow them to save it in their password manager for easy retrieval in the future. On average, an individual has over 168 passwords for several accounts. That’s a lot already, and enabling password managers saves your users a ton of stress while reducing the need to ‘forget password’ each time.
➢ Offer Secure “Remember Me” Options
To prevent recurrent double-layered authentication, you can offer the “Remember Me” option. This will help your server recognize a user’s device the next time they log in again. So, instead of requiring extra security checks every time, your system issues a long-lived, secure token tied to that device, allowing the user to log in more smoothly while still staying protected.
➢ Make Password Reset Easy but Safe
Reduce the checkpoints to resetting the user password as much as possible. If needed, you can ask users to confirm some secret security questions or DOB before you send them a reset link. If they fail the questions, you can request that they provide additional details for a reset.
Also, ensure your password reset links are sent through secure and recognizable channels. If you use email for credential delivery, consider using an enterprise email service to provide high-level security standards, including multi-layered protection, encryption, and tamper-proof archiving.
➢ Show Clear & Non-Generic Error Messages
Display clearly the reason for failed logins beyond just red and bouncing bars. If the password or username is incorrect, inform them. If the user enters an old password that has already been changed, tell them so they can recall the new one. Be as clear as possible when a login fails.
➢ Use Mobile-Friendly Login Design
Login pages do not necessarily need much aesthetic appeal, but they shouldn’t look wobbly either. Employ good themes that look good on both mobile and non-mobile devices. Your page should naturally fit within the frames of different devices, be easily navigable, and also easily located by users.
➢ Provide Login Notifications
Whenever a user logs in, ensure they also receive a push notification on their registered device, via email or SMS. The security benefit is that if there’s unauthorized access, they are quickly informed and can make a complaint or change their password, and cancel ongoing sessions before more harm is done.
Also Read: Best Technology For Website Development
Common Mistakes to Avoid
Simple mistakes can cost your website and users significantly, ranging from financial loss to legal implications and damage to brand trust. Here are some common ones to avoid:
- Using HTTP instead of HTTPS
- Weak password policies
- Failure to implement rate limiting for login attempts
- Exposed login endpoints
- Not invalidating sessions when passive or during logouts
- Storing passwords in plain text
- Lack of MFA or 2FA
Follow the steps we discussed earlier to create a secure login system to eliminate these mistakes.
Also Read: Do Websites Go Away with AI Agents
Conclusion
There’s an uptrend in the number of website hacks, and millions of user passwords are compromised every quarter. You need to protect your website and users by creating a secure login system, both on the frontend and backend.
Start by implementing HTTPS, enabling secure password storage techniques, and enforcing strong password creation policies. Implement MFA/2FA, limit login attempts, and ensure your login forms are safe.
In addition, follow best practices for session management, such as invalidating passive or outdated sessions. Monitor and log every login attempt, enable SSO to unify access, and regularly audit your security measures to keep up.
Frequently Asked Questions
Authentication is the process of verifying a user’s identity to allow login, while authorization determines what the user can do or access once logged in and to what extent.
Strong authentication prevents cyberattackers from accessing your website and stealing users’ data. This protects your users from extortion and saves your business from legal implications while protecting your reputation.
Never store user passwords in plain text. Implement strong hashing algorithms, such as bcrypt, and use salting to foil randomized guessing. Also consider peppering before saving passwords in your database.
MFA requires your users to provide two or more factors—something they know (such as a password), something they have (like a phone or token), or something they are (like a biometric). Yes, you should enable MFA, as it is an extra layer of security for your website.
Implement rate limiting, lockouts after repeated failures, CAPTCHA, MFA, and monitoring tools to detect suspicious login activity.